SPOILER ALERT!
2 Israeli teens arrested after DDoS 'booter' service vDOS hacked
To date, for instance, it's unclear if the document-setting DDoS attacks tied to contaminated internet of things gadgets - and IoT malware corresponding to Mirai - have been launched by stresser/booter services. But traditionally, cybercriminals have only infected large numbers of IoT gadgets to monetize their efforts by providing on-demand DDoS assaults. You stand a greater chance of withstanding a DDoS assault if your Web server is positioned in a hosting middle than should you run it yourself. That's as a result of its data heart will likely have far greater bandwidth links and higher capability routers than your organization has, and its workers will probably have extra expertise coping with assaults.
Booter and stresser companies are a form of DDoS-for-hire--- advertised in discussion board communications and out there on Dark Web marketplaces--- offering malicious actors the flexibility to anonymously assault any Internet-linked target. These providers are obtained by way of a financial transaction, normally in the form of online cost providers and virtual forex. IP booters, also called IP stressers, are companies that have been dropped at life within the early 2010s and gained big traction for the convenience of accessibility. These companies allowed for anybody to provoke DDoS attacks by renting another person’s infrastructure for a cheap month-to-month price — some as cheap as $2.
This analysis is still in its initial part and will contribute to a Ph.D. thesis after 4 years. An Ars analysis of theLizardStresser database found that the service launched nearly sixteen,000 individual attacks over the past month, targeting just over 3,900 IP addresses. ddos stresser free of those assaults—sixty seven %—targeted widespread Web server ports (port eighty and 8080 for HTTP; and a small however important variety of attacks on port 443 for HTTPS). The next most popular goal—accounting for nearly 7 % of the assaults—was port 25565, the network port used by Minecraft servers. Most booting companies at present are utilizing cloud-primarily based hosting to leverage their community.
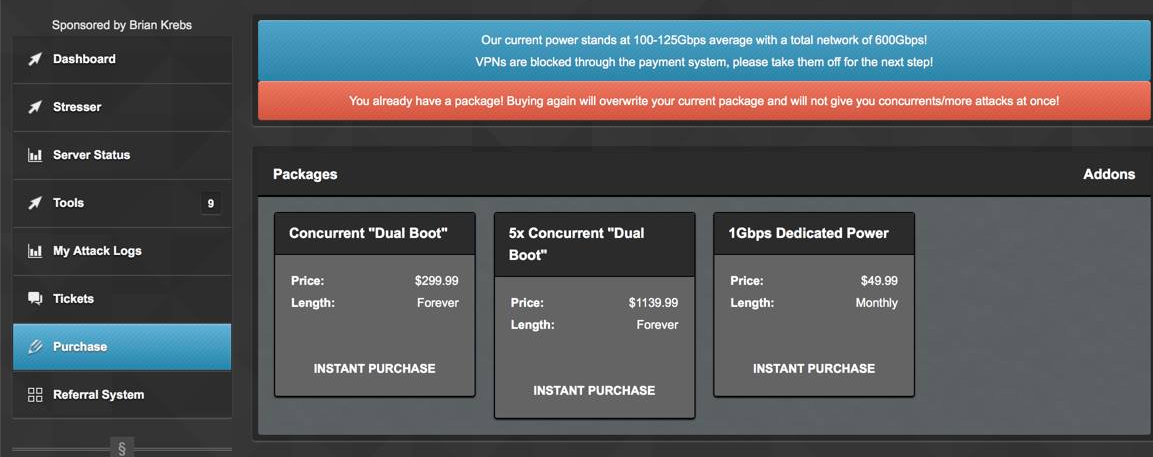
Distributed Denial of Service (DDoS) attacks are an growing risk on the Internet. Until a few years in the past, these types of assaults had been only launched by individuals with superior data of computer networks. However, these days the power to launch attacks have been supplied as a service to everyone, even to these with none advanced data. Some of them promote, for less than U$ 5, up to 25 Gbps of DDoS visitors, which is greater than sufficient to make most hosts and providers on the Internet unavailable. Booters are rising in recognition and they have shown the success of attacks towards third celebration services, corresponding to government web sites; nonetheless, there are few mitigation proposals.
In addition, present literature in this area supplies solely a partial understanding of the risk, for instance by analyzing just a few elements of one specific Booter. In this paper, we suggest mitigation options towards DDoS-as-a-Service that might be achieved after an intensive characterization of Booters. Early outcomes present fifty nine completely different Booters, which some of them don't deliver what is offered.
Having your Web server situated with a hoster may also keep DDoS traffic geared toward your Web server off your corporate LAN so at least that a part of your corporation – together with email and presumably voice over IP (VoIP) providers – should operate usually during an assault. Figures posted to the house page of Ragebooter.internet declare the service has been used to conduct greater than 310,000 DDoS assaults. Memberships are offered in packages ranging from $3 per day to $300 a year for an “enterprise” plan.
Ragebooter[dot]net includes a notice at the prime of the location indicating that rageservices[dot]internet is indeed affiliated with Ragebooter. DDoS (Distributed Denial of Service) attacks attempt to make servers or networks quickly unavailable to customers. Most of us would, indeed, suppose that solely folks with high technical skills would be able to carry out such assaults, however that is not true. ps4 booter can use the so known as ‘Booter’ web sites to disrupt on-line services and Jose Jair Cardoso de Santanna, a PhD candidate from the Design and Analysis of Communication Systems group, is aiming to mitigate that. DE-CIX’s Daniel Kopp presented preliminary outcomes at the RIPE77 assembly in Amsterdam last week.
For instance, ExoStresser was used to launch DDoS attacks towards a major video game producer, and a Pennsylvania scholar used BetaBooter to attack her college's network, also bringing down the IT systems of 17 different organizations in a domino effect. "DDoS attacks continue to develop in depth and complexity, with many attacks blending network and utility layer attacks," the IOCTA report reads. "Booters/stressers are readily available as-a-service, accounting for an rising number of DDoS assaults." Such providers are sometimes additionally used to extort victims. On-demand DDoS assaults could be robust to trace, especially if service operators use contaminated endpoints to launch their attacks.
By utilizing cloud providers to host their assault scripts they are able to provide bigger bandwidth for his or her attacks. Owners behind these stresser providers only have a couple of expenses to get their service up and running. These servers should enable IP handle spoofing, have a quick uplink, 1Gbps+, and have unmetered bandwidth usage. Once the proprietor has their servers, all they have to do is setup the service by importing the shell of their selection. US authorities began an investigation into Usatyuk's services after his websites were on the center of many DDoS attacks in 2016.
Booter and stresser companies are a form of DDoS-for-hire--- advertised in discussion board communications and out there on Dark Web marketplaces--- offering malicious actors the flexibility to anonymously assault any Internet-linked target. These providers are obtained by way of a financial transaction, normally in the form of online cost providers and virtual forex. IP booters, also called IP stressers, are companies that have been dropped at life within the early 2010s and gained big traction for the convenience of accessibility. These companies allowed for anybody to provoke DDoS attacks by renting another person’s infrastructure for a cheap month-to-month price — some as cheap as $2.
This analysis is still in its initial part and will contribute to a Ph.D. thesis after 4 years. An Ars analysis of theLizardStresser database found that the service launched nearly sixteen,000 individual attacks over the past month, targeting just over 3,900 IP addresses. ddos stresser free of those assaults—sixty seven %—targeted widespread Web server ports (port eighty and 8080 for HTTP; and a small however important variety of attacks on port 443 for HTTPS). The next most popular goal—accounting for nearly 7 % of the assaults—was port 25565, the network port used by Minecraft servers. Most booting companies at present are utilizing cloud-primarily based hosting to leverage their community.

Distributed Denial of Service (DDoS) attacks are an growing risk on the Internet. Until a few years in the past, these types of assaults had been only launched by individuals with superior data of computer networks. However, these days the power to launch attacks have been supplied as a service to everyone, even to these with none advanced data. Some of them promote, for less than U$ 5, up to 25 Gbps of DDoS visitors, which is greater than sufficient to make most hosts and providers on the Internet unavailable. Booters are rising in recognition and they have shown the success of attacks towards third celebration services, corresponding to government web sites; nonetheless, there are few mitigation proposals.
In addition, present literature in this area supplies solely a partial understanding of the risk, for instance by analyzing just a few elements of one specific Booter. In this paper, we suggest mitigation options towards DDoS-as-a-Service that might be achieved after an intensive characterization of Booters. Early outcomes present fifty nine completely different Booters, which some of them don't deliver what is offered.
Having your Web server situated with a hoster may also keep DDoS traffic geared toward your Web server off your corporate LAN so at least that a part of your corporation – together with email and presumably voice over IP (VoIP) providers – should operate usually during an assault. Figures posted to the house page of Ragebooter.internet declare the service has been used to conduct greater than 310,000 DDoS assaults. Memberships are offered in packages ranging from $3 per day to $300 a year for an “enterprise” plan.
Ragebooter[dot]net includes a notice at the prime of the location indicating that rageservices[dot]internet is indeed affiliated with Ragebooter. DDoS (Distributed Denial of Service) attacks attempt to make servers or networks quickly unavailable to customers. Most of us would, indeed, suppose that solely folks with high technical skills would be able to carry out such assaults, however that is not true. ps4 booter can use the so known as ‘Booter’ web sites to disrupt on-line services and Jose Jair Cardoso de Santanna, a PhD candidate from the Design and Analysis of Communication Systems group, is aiming to mitigate that. DE-CIX’s Daniel Kopp presented preliminary outcomes at the RIPE77 assembly in Amsterdam last week.
For instance, ExoStresser was used to launch DDoS attacks towards a major video game producer, and a Pennsylvania scholar used BetaBooter to attack her college's network, also bringing down the IT systems of 17 different organizations in a domino effect. "DDoS attacks continue to develop in depth and complexity, with many attacks blending network and utility layer attacks," the IOCTA report reads. "Booters/stressers are readily available as-a-service, accounting for an rising number of DDoS assaults." Such providers are sometimes additionally used to extort victims. On-demand DDoS assaults could be robust to trace, especially if service operators use contaminated endpoints to launch their attacks.
Understanding DDoS internals: Measuring booter providers
By utilizing cloud providers to host their assault scripts they are able to provide bigger bandwidth for his or her attacks. Owners behind these stresser providers only have a couple of expenses to get their service up and running. These servers should enable IP handle spoofing, have a quick uplink, 1Gbps+, and have unmetered bandwidth usage. Once the proprietor has their servers, all they have to do is setup the service by importing the shell of their selection. US authorities began an investigation into Usatyuk's services after his websites were on the center of many DDoS attacks in 2016.
SPOILER ALERT!
Man who made $542,925 renting out DDoS services sentenced to prison – HOTforSecurity
Whatever illusions booter service operators or customers might have harbored about their actions should have been dispelled following a chat delivered at the Black Hat security conference in Las Vegas this year. In that speech,FBI Agent Elliott Peterson issued an unambiguous warning that the company was ready to investigate and assist prosecute individuals engaged in selling and shopping for from booter companies.
An Illinois man pleaded responsible at present for operating eight DDoS booter (stresser) services between August 2015 and November 2017. We've picked up some unusual traffic out of your community and have briefly blocked entry from your IP tackle. James mentioned the information was handed off to regulation enforcement, and the particular Booter service that initially attacked Krebs was shut down within a short period of time. quezstresser in taking down the Booter service has to do with the truth that the Internet service provider (ISP) that the service seems like it's being hosted from isn't the place the Booter service actually is located.
In it, Huri signs his actual name and says he's 18 years previous and about to be drafted into the Israel Defense Forces. Bidani co-authored the paper under the alias “,” an e mail address that I identified in my previous reporting was assigned to one of the directors of vDOS. As I described on this week’s story, vDOS is a “booter” service that has earned in extra of $600,000 over the past two years serving to customers coordinate more than a hundred and fifty,000 so-referred to as distributed denial-of-service (DDoS) attacks designed to knock Web sites offline. Two young Israeli males alleged to be the co-homeowners of a preferred online assault-for-hire service had been reportedly arrested in Israel on Thursday.
In response to their investigations, PayPal began seizing booter service PayPal accounts and balances, effectively launching their very own preemptive denial-of-service assaults against the fee infrastructure for these providers. The researchers found that their interventions cut profits in half for the popular booter service, and helped scale back the number of attacks popping out of it by at least 40 p.c. Reaper was primarily based in part on “Mirai,” IoT malware code designed to knock Web websites offline in excessive-powered information floods, and an IoT malware pressure that powered many of the largest cyberattacks of the previous year. So it’s worrisome to suppose somebody could have simply constructed an army of one million IoT drones that could possibly be utilized in crippling, coordinated assaults able to wiping most networks offline.
ddos stresser reveals that they now use an intermediary server (forty five.fifty five.55.193) to handle Coinbase traffic. When a Bitcoin fee is acquired, Coinbase notifies this middleman server, not the actual vDOS servers in Bulgaria.
The brevity of such hijacks makes them considerably ineffective at mitigating massive-scale DDoS attacks, which often final for hours at a time. For example, the BGP hijack that BackConnect launched towards Verdina lasted a fraction of an hour, and according to the corporate’s CEO was launched solely after the DDoS attack subsided. In that 2015 paper, the researchers said they deployed 21 globally-distributed AmpPot situations, which noticed more than 1.5 million assaults between February and May 2015.
The pair had been arrested across the identical time that KrebsOnSecurity revealed a narrative naming them because the masterminds behind a service that can be hired to knock Web websites and Internet users offline with powerful blasts of junk data. For starters, malicious BGP assaults designed to collect information about an attacking host are more likely to be very brief — often lasting only a few minutes.
Lance James, chief scientist at Vigilant, defined to eWEEK that he received pulled into an investigation into the world of Booter services by his friend, safety blogger Brian Krebs. Krebs had been the sufferer of a Booter service attack and was in search of some answers. The DOJ famous that booter-based mostly DDoS assault instruments provide a low barrier to entry for customers trying to have interaction in cybercrime. Indeed, hiring a service to paralyze your enemies’, your competition’s and/or your targets’ sites makes it as straightforward as simply handing over the money, no technical ability required. It is apparent from the leaked vDOS logs that in July 2016 the service’s homeowners implemented an extra safety measure for Bitcoin funds, which they accept through Coinbase.

On Friday, Oct. 28, Jesse LaBrocca — the administrator of the favored English-language hacking discussion board Hackforums[dot]internet — said he was shutting down the “server stress testing” (SST) section of the forum. The move comes amid heightened public scrutiny of the SST business, which has been linked to a number of unusually highly effective current assaults and is liable for the overwhelming majority of denial-of-service (DOS) assaults on the Internet at present. As detailed in August 2015’s “Stress-Testing the Booter Services, Financially,” the researchers posed as buyers of almost two dozen booter companies — including vDOS — in a bid to find the PayPal accounts that booter providers had been utilizing to accept funds.
Although I can’t prove it but, it appears likely that vDOS is answerable for a number of a long time worth of DDoS years. That’s as a result of the info leaked within the hack of vDOS recommend that the proprietors erased all digital data of assaults that customers launched between Sept. 2012 (when the service first came online) and the top of March 2016. At the top of August 2016, Huri and Bidani authored a technical paper (PDF) on DDoS attack strategies which was revealed within the Israeli security e-zine Digital Whisper.
Analyzing the assaults extra intently, they found that more than 96% of the attacks stem from single sources, similar to booter companies. But the back end of the booter service is where the actually interesting stuff happens.
These new, off-the-shelf attack providers are commoditizing the artwork of hacking, making it possible for novice hackers with little know-tips on how to launch assaults via reasonably priced tools which might be out there on the Darknet and the Clearnet. To add humor into the situation, most DDoS-as-a-service web sites use DDoS mitigation companies to stop their competitors from taking them offline. Between August 2015 to November 2017 Sergiy P. Usatyuk of Orland Park, Illinois, and a co-conspirator, operated numerous “booter” providers that launched millions of distributed denial-of-service attacks that rendered websites slow or inaccessible. Court paperwork say users who signed up on Usatyuk's sites launched 3,829,812 DDoS attacks towards 1000's of firms, inflicting tons of of hundreds of downtime.
An Illinois man pleaded responsible at present for operating eight DDoS booter (stresser) services between August 2015 and November 2017. We've picked up some unusual traffic out of your community and have briefly blocked entry from your IP tackle. James mentioned the information was handed off to regulation enforcement, and the particular Booter service that initially attacked Krebs was shut down within a short period of time. quezstresser in taking down the Booter service has to do with the truth that the Internet service provider (ISP) that the service seems like it's being hosted from isn't the place the Booter service actually is located.
In it, Huri signs his actual name and says he's 18 years previous and about to be drafted into the Israel Defense Forces. Bidani co-authored the paper under the alias “,” an e mail address that I identified in my previous reporting was assigned to one of the directors of vDOS. As I described on this week’s story, vDOS is a “booter” service that has earned in extra of $600,000 over the past two years serving to customers coordinate more than a hundred and fifty,000 so-referred to as distributed denial-of-service (DDoS) attacks designed to knock Web sites offline. Two young Israeli males alleged to be the co-homeowners of a preferred online assault-for-hire service had been reportedly arrested in Israel on Thursday.
DDoS Top 6: Why Hackers Attack
In response to their investigations, PayPal began seizing booter service PayPal accounts and balances, effectively launching their very own preemptive denial-of-service assaults against the fee infrastructure for these providers. The researchers found that their interventions cut profits in half for the popular booter service, and helped scale back the number of attacks popping out of it by at least 40 p.c. Reaper was primarily based in part on “Mirai,” IoT malware code designed to knock Web websites offline in excessive-powered information floods, and an IoT malware pressure that powered many of the largest cyberattacks of the previous year. So it’s worrisome to suppose somebody could have simply constructed an army of one million IoT drones that could possibly be utilized in crippling, coordinated assaults able to wiping most networks offline.
ddos stresser reveals that they now use an intermediary server (forty five.fifty five.55.193) to handle Coinbase traffic. When a Bitcoin fee is acquired, Coinbase notifies this middleman server, not the actual vDOS servers in Bulgaria.
The brevity of such hijacks makes them considerably ineffective at mitigating massive-scale DDoS attacks, which often final for hours at a time. For example, the BGP hijack that BackConnect launched towards Verdina lasted a fraction of an hour, and according to the corporate’s CEO was launched solely after the DDoS attack subsided. In that 2015 paper, the researchers said they deployed 21 globally-distributed AmpPot situations, which noticed more than 1.5 million assaults between February and May 2015.
The pair had been arrested across the identical time that KrebsOnSecurity revealed a narrative naming them because the masterminds behind a service that can be hired to knock Web websites and Internet users offline with powerful blasts of junk data. For starters, malicious BGP assaults designed to collect information about an attacking host are more likely to be very brief — often lasting only a few minutes.
Following the Money Hobbled vDOS Attack-for-Hire Service
Lance James, chief scientist at Vigilant, defined to eWEEK that he received pulled into an investigation into the world of Booter services by his friend, safety blogger Brian Krebs. Krebs had been the sufferer of a Booter service attack and was in search of some answers. The DOJ famous that booter-based mostly DDoS assault instruments provide a low barrier to entry for customers trying to have interaction in cybercrime. Indeed, hiring a service to paralyze your enemies’, your competition’s and/or your targets’ sites makes it as straightforward as simply handing over the money, no technical ability required. It is apparent from the leaked vDOS logs that in July 2016 the service’s homeowners implemented an extra safety measure for Bitcoin funds, which they accept through Coinbase.

On Friday, Oct. 28, Jesse LaBrocca — the administrator of the favored English-language hacking discussion board Hackforums[dot]internet — said he was shutting down the “server stress testing” (SST) section of the forum. The move comes amid heightened public scrutiny of the SST business, which has been linked to a number of unusually highly effective current assaults and is liable for the overwhelming majority of denial-of-service (DOS) assaults on the Internet at present. As detailed in August 2015’s “Stress-Testing the Booter Services, Financially,” the researchers posed as buyers of almost two dozen booter companies — including vDOS — in a bid to find the PayPal accounts that booter providers had been utilizing to accept funds.
Although I can’t prove it but, it appears likely that vDOS is answerable for a number of a long time worth of DDoS years. That’s as a result of the info leaked within the hack of vDOS recommend that the proprietors erased all digital data of assaults that customers launched between Sept. 2012 (when the service first came online) and the top of March 2016. At the top of August 2016, Huri and Bidani authored a technical paper (PDF) on DDoS attack strategies which was revealed within the Israeli security e-zine Digital Whisper.
Analyzing the assaults extra intently, they found that more than 96% of the attacks stem from single sources, similar to booter companies. But the back end of the booter service is where the actually interesting stuff happens.
These new, off-the-shelf attack providers are commoditizing the artwork of hacking, making it possible for novice hackers with little know-tips on how to launch assaults via reasonably priced tools which might be out there on the Darknet and the Clearnet. To add humor into the situation, most DDoS-as-a-service web sites use DDoS mitigation companies to stop their competitors from taking them offline. Between August 2015 to November 2017 Sergiy P. Usatyuk of Orland Park, Illinois, and a co-conspirator, operated numerous “booter” providers that launched millions of distributed denial-of-service attacks that rendered websites slow or inaccessible. Court paperwork say users who signed up on Usatyuk's sites launched 3,829,812 DDoS attacks towards 1000's of firms, inflicting tons of of hundreds of downtime.
SPOILER ALERT!
Lizard Squad's LizardStresser booter run on 'hacked house routers'
I actually have a Google Pixel three XL, so I’ll describe the instructions to seek out an IP handle on that. best stresser might be related, however these instructions may not precisely match depending on what you’re utilizing.
While a booter that does not use any third-party methods without permission might in principle be justified beneath sure conditions, the authors argue that it's unlikely that any present booters meet these necessities. A 20-yr-old Illinois man pleaded responsible to expenses related to a scheme to launch hundreds of thousands of distributed denial-of-service attacks in opposition to U.S. college districts and different targets, the U.S.
The illegal web sites operated by Usatyuk had vibrant names corresponding to ExoStresser, QuezStresser, Betabooter, Databooter, Instabooter, Polystress, and Zstress. A 21-year-previous man who made half 1,000,000 dollars working DDoS-for-hire providers has been sentenced to jail for 13 months. Authorities tracked down Usatyuk despite the suspect discussing with his co-conspirator about removing server entry logs to cover evidence following the excessive-profile arrest of a similar DDoS booter operator in the UK. "You can DDOS any IP you need, we do not care," Usatyuk mentioned in certainly one of his HackForums posts before the discussion board's administrators determined to ban the promoting of DDoS booters on their site altogether, back in October 2016.
At the peak of vDOS’s profitability in mid-2015, the DDoS-for-rent service was incomes its proprietors greater than $42,000 a month in PayPal and Bitcoin payments from 1000's of subscribers. That’s according to an evaluation of the leaked vDOS database performed by researchers at New York University. That preliminary vDOS story was primarily based on knowledge shared by an nameless supply who had hacked vDOS and obtained its non-public person and attack database.
Incredibly, for transient periods the positioning even accepted credit cards in change for online attacks, although it’s unclear how much the location might have made in credit card payments because the data isn't in the leaked databases. ip stresser paypal from Saarland University in Germany, as well as the Yokohama National University and National Institute of Information and Communications Technology — each in Japan. In a years-lengthy venture first detailed in 2015, the researchers seemed for scanning that appeared to be kicked off by ne’er-do-wells running booter services.
Authorities said Usatyuk ran these companies on high of a botnet comprised of no less than 31 highly effective servers that the two rented from two US cloud internet hosting suppliers. During the interval of the conspiracy, Usatyuk and a co-conspirator gained in extra of $550,000 from charging subscriber fees to paying customers of their booter companies and selling advertising house to different booter operators. Specifically in the complaint, the Justice Department accused Downthem had greater than 2,000 customer subscriptions, and had been used to hold out over 200,000 attacks. You may remember Lizard Squad because the Grinch who ruined players’ Christmas with a DDoS in opposition to the servers that power PlayStation and Xbox consoles – an assault it carried out for our personal good. One instance is Lizard Squad, which, until its operators have been busted in 2016, rented out its LizardStresser assault service.

In this kind of assault, the attacker sends a message to a 3rd celebration, while spoofing the Internet handle of the sufferer. When the third get together replies to the message, the reply is sent to the sufferer — and the reply is way larger than the original message, thereby amplifying the size of the assault. Vendors who wish to “sticky” their adverts — that's, pay to maintain the adverts displayed prominently close to or at the top of a given dialogue subforum — pay LaBrocca up to $60 per week for the prime sticky spots.
In December, authorities within the United States filed criminal costs in opposition to three males accused of operating booter services, and orchestrated a coordinated takedown of 15 totally different booter sites. Tap on your Settings app, and then faucet on “Wi-Fi.” Tap on the “i” with a circle in it to the proper of whatever community you’re linked to, and you’ll see your IPv4 tackle proper there—and your IPv6 address right below it.
An attack service that was, suitably sufficient, given a dose of its own drugs when it was hacked in 2015. They did this as a result of on the time PayPal was working with a team of academic researchers to establish, seize and shutter PayPal accounts that have been discovered to be accepting funds on behalf of booter companies like vDOS. Anyone excited about studying more on their success in making life more durable for these booter service homeowners should take a look at my August 2015 story,Stress-Testing the Booter Services, Financially.
The story showed how the service made roughly $600,000 over just two of the four years it was in operation. Most of those income came within the form of bank card payments by way of PayPal. Now some botnet specialists are calling on individuals to stop the “Reaper Madness,” saying the actual variety of IoT units contaminated with Reaper proper now could be a lot smaller. Operation Power Off is a part of a broader law enforcement effort to disrupt the burgeoning booter service business and to weaken demand for such companies.
Getting your inner IP handle is slightly more complicated than clicking on a hyperlink, nevertheless it’s not that robust. Look in your occasion’s IPv4 Public IP, which is the handle of the server.
While a booter that does not use any third-party methods without permission might in principle be justified beneath sure conditions, the authors argue that it's unlikely that any present booters meet these necessities. A 20-yr-old Illinois man pleaded responsible to expenses related to a scheme to launch hundreds of thousands of distributed denial-of-service attacks in opposition to U.S. college districts and different targets, the U.S.
The illegal web sites operated by Usatyuk had vibrant names corresponding to ExoStresser, QuezStresser, Betabooter, Databooter, Instabooter, Polystress, and Zstress. A 21-year-previous man who made half 1,000,000 dollars working DDoS-for-hire providers has been sentenced to jail for 13 months. Authorities tracked down Usatyuk despite the suspect discussing with his co-conspirator about removing server entry logs to cover evidence following the excessive-profile arrest of a similar DDoS booter operator in the UK. "You can DDOS any IP you need, we do not care," Usatyuk mentioned in certainly one of his HackForums posts before the discussion board's administrators determined to ban the promoting of DDoS booters on their site altogether, back in October 2016.
At the peak of vDOS’s profitability in mid-2015, the DDoS-for-rent service was incomes its proprietors greater than $42,000 a month in PayPal and Bitcoin payments from 1000's of subscribers. That’s according to an evaluation of the leaked vDOS database performed by researchers at New York University. That preliminary vDOS story was primarily based on knowledge shared by an nameless supply who had hacked vDOS and obtained its non-public person and attack database.
Incredibly, for transient periods the positioning even accepted credit cards in change for online attacks, although it’s unclear how much the location might have made in credit card payments because the data isn't in the leaked databases. ip stresser paypal from Saarland University in Germany, as well as the Yokohama National University and National Institute of Information and Communications Technology — each in Japan. In a years-lengthy venture first detailed in 2015, the researchers seemed for scanning that appeared to be kicked off by ne’er-do-wells running booter services.
Security Considerations for a Blended Workforce
Authorities said Usatyuk ran these companies on high of a botnet comprised of no less than 31 highly effective servers that the two rented from two US cloud internet hosting suppliers. During the interval of the conspiracy, Usatyuk and a co-conspirator gained in extra of $550,000 from charging subscriber fees to paying customers of their booter companies and selling advertising house to different booter operators. Specifically in the complaint, the Justice Department accused Downthem had greater than 2,000 customer subscriptions, and had been used to hold out over 200,000 attacks. You may remember Lizard Squad because the Grinch who ruined players’ Christmas with a DDoS in opposition to the servers that power PlayStation and Xbox consoles – an assault it carried out for our personal good. One instance is Lizard Squad, which, until its operators have been busted in 2016, rented out its LizardStresser assault service.

In this kind of assault, the attacker sends a message to a 3rd celebration, while spoofing the Internet handle of the sufferer. When the third get together replies to the message, the reply is sent to the sufferer — and the reply is way larger than the original message, thereby amplifying the size of the assault. Vendors who wish to “sticky” their adverts — that's, pay to maintain the adverts displayed prominently close to or at the top of a given dialogue subforum — pay LaBrocca up to $60 per week for the prime sticky spots.
In December, authorities within the United States filed criminal costs in opposition to three males accused of operating booter services, and orchestrated a coordinated takedown of 15 totally different booter sites. Tap on your Settings app, and then faucet on “Wi-Fi.” Tap on the “i” with a circle in it to the proper of whatever community you’re linked to, and you’ll see your IPv4 tackle proper there—and your IPv6 address right below it.
An attack service that was, suitably sufficient, given a dose of its own drugs when it was hacked in 2015. They did this as a result of on the time PayPal was working with a team of academic researchers to establish, seize and shutter PayPal accounts that have been discovered to be accepting funds on behalf of booter companies like vDOS. Anyone excited about studying more on their success in making life more durable for these booter service homeowners should take a look at my August 2015 story,Stress-Testing the Booter Services, Financially.
The story showed how the service made roughly $600,000 over just two of the four years it was in operation. Most of those income came within the form of bank card payments by way of PayPal. Now some botnet specialists are calling on individuals to stop the “Reaper Madness,” saying the actual variety of IoT units contaminated with Reaper proper now could be a lot smaller. Operation Power Off is a part of a broader law enforcement effort to disrupt the burgeoning booter service business and to weaken demand for such companies.
Getting your inner IP handle is slightly more complicated than clicking on a hyperlink, nevertheless it’s not that robust. Look in your occasion’s IPv4 Public IP, which is the handle of the server.
SPOILER ALERT!
How much cost a DDoS assault service? Which elements affect the final value?Security Affairs
Dutch police shut down 15 DDoS-for-hire platforms
A DDoS attack overwhelms a site, causing it to collapse beneath the load of malicious traffic. In October the FBI launched an advisory warning that using booter services, additionally called “stressers”, is punishable under the Computer Fraud and Abuse Act, and will end in arrest and felony prosecution. Poland’s Facebook page says he's the proprietor of Ragebooter[dot]com, Ragebooter[dot]internet, and one other site known as vmdeploy[net]. The commercial for Ragebooter’s new mobile app on Google Play says the developer’s email tackle is [dot]internet. The registration details for Rageservices[dot]net are hidden, but the Web site lists some helpful contact particulars.
To know exactly how they work, I decided to first carry out an assault by myself residential network and later on the college’, clarifies Santanna. Based on particular person examples, we understood that for NTP mirrored attacks the highest three ASes have been liable for 23% of the visitors, coming from China, Taiwan, and Hungary, whereas memchached assaults primarily originated in Europe.
The future work will focus on designing simpler mitigation strategies and on better understanding the anatomy of such assaults in an Internet Exchange context. According to Arbor Network’s BladeRunner, from July to October the Forceful’s booter bot was rented for eighty two assaults equaling $5,408. According to the data elaborated by the experts, a booter attack could trigger US$7.2 million in damages a day, prices that could be drastically lowered by the adoption of DDoS defense solutions. We have discussed a number of occasions about the idea ofcybercrime-as-a-service, at present I’ll show you a case associated the offer for lease ofdistributed-denial-of-service(DDoS) attacks for less than US$60 per day. Europol is using the operation to kick off a prevention marketing campaign to warn younger, would-be customers of DDoS stresser providers corresponding to Netspoof.
ddos booter online seized 15 internet domains associated with DDoS-for-hire providers and announced felony expenses against three people charged with operating the platforms. DDoS-for-hire services – also known as ‘DDoS stressors’ or ‘booters’ – sell access to botnets comprising principally compromised machines that serve as launchpads for DDoS assaults. Prices for 0x-booter service range from $20 to $a hundred and fifty, depending on the variety of assaults, the length of an attack, and buyer support.
DDoS stands for Distributed Denial of Service, a malicious attempt to make a server or a network resource unavailable to reliable users, by overloading it with large amounts of fake visitors. Distributed Denial of Service attacks have increased in scale, intensity and frequency.
The wide range of motives for these assaults – political (hacktivism), felony (coercion), or social (malice) – makes each merchant or organization with an online presence a possible target. The shared nature of the Internet infrastructure – whether or not hosting, DNS, or bandwidth – places many retailers or organizations susceptible to becoming collateral damage, as well. If you find that your website or organization is underneath assault, it’s important that you just report such assaults quickly to parties which might be greatest positioned that will help you mitigate, climate, and restore normal service.
In right now’s present cybercrime economy, a number of dollars mixed with malicious intent may be interprets to considerable harm to just about any target. The attacks we now have seen from this booter where not very efficient and were automatically mitigated by Deflect.
It’s a quite simple software actually, you just must fill within the URL or IP tackle of the target system, choose the assault methodology and port and press the massive button that claims “IMMA CHARGIN MAH LAZER”. Payment for booter and stresser assaults had been usually collected by way of Paypal, he said, which opened up one avenue for disrupting the way they work. "They have lots of paying clients and we see hundreds of 1000's of attacks from these providers annually," he advised the BBC in an interview carried out before Black Hat. "Booter operators are heavy customers of social media and it is not difficult to seek out out who they're and the place they're from," mentioned Agent Peterson. Operators ranged in age from however most companies were run by folks in their teens, he mentioned.

It isn’t nice to think that your website could fall victim to a DDoS attack. It’s even worse to think that the attack might come from someone hiding behind a Booter. Our staff is skilled within the Stress Testing Service space and able of providing the most effective net stresser with dedicated energy and developed assault methods to bypass the latest Anti-DDoS protections.
The back-doored joomla file and the jsb.js Javascript device (with a reference to a Turkish hacker discussion board) let us suppose that we've here a very newbie group that reused different tools shared on hacker forums, and indicate a low technical talent degree. One attention-grabbing factor to notice, is that the sockhit.php file does not appear to require authentication, which signifies that the infrastructure might have been used by other folks unknowingly of the owners. We think that these PHP recordsdata are not immediately launching the attacks however rather utilizing the totally different tools deployed on the server to do this. We could not download these php information (sockhit.php and api.php), but we may rapidly deduce that they had been used to remotely command the booter server from the interface to launch assaults. Finally, a small a part of these requests remained from unknown sources till we found the Joomla relay listing on the booter servers (see after).
Internet Crime Complaint Center
Criminal actors supply distributed denial of service (DDoS)-for-rent companies in felony forums and marketplaces. These DDoS-for-hire companies, also known as booters or stressers, are leveraged by malicious cyber actors, pranksters, and/or hacktivists to conduct largescale cyber attacks designed to prevent entry to U.S. firm and authorities Web websites. top booter investigates these companies as a criminal offense if they are used towards a Web web site with out the proprietor’s permission (similar to for a respectable stress test). Distributed Denial-of-Service (DDoS) service offerings, typically disguised as legitimate “booter” or “stresser” providers, continue to extend within the cyber underground market.
Europol’s European Cybercrime Centresaid Mondayit carried out the operation from Dec. 5 to 9. To give you an instance of the price-friendliness of this lovely service, one pattern Booter costs $40 USD/month (£25) for an unlimited number of DDoS attacks lasting one hour. According to the release, Downthem’s database showed over 2000 buyer subscriptions, and had been used to conduct, or attempt to conduct, over 200,000 DDoS assaults which have been carried out between October 2014 and November 2018.
How your computer acts when infected depends on what the cybercriminals are trying to accomplish. Many botnets are designed to harvest knowledge, corresponding to passwords, social safety numbers, bank card numbers, addresses, telephone numbers, and other private data. The data is then used for nefarious functions, corresponding to identification theft, credit card fraud, spamming, and malware distribution.
Bots may also be used to launch attacks on websites and networks, which as are sometimes referred to as Distributed Denial of Service Attacks or DDoS. In reality, in a latest survey practically half the responding companies mentioned that they believed that their opponents were launching DDoS assaults in order to disrupt services.
Just set up a free proxy with Amazon Web Services to guard your server from denial-of-service attacks. DDoSPedia is a glossary that focuses on community and software safety terms with many distributed denial-of-service (DDoS)-associated definitions. It provides a central place for onerous to search out web-scattered definitions on DDoS attacks.
After all, if your competition’s website is down, all the visitors will come to your website as an alternative. Additionally, your competition’s model image is tarnished, giving optimistic associations to your organization instead. A proxy server is an middleman server through which your visitors will get routed. The web servers you go to see solely the IP address of that proxy server and never your IP tackle.
Since then, he stated, many had diversified to supply "stresser" providers that attempt to overwhelm a target website with knowledge in what is named a distributed denial of service (DDoS) attack. The problem is that legal organisations are abusing booters for unlawful DDoS assaults, one of the most well-liked examples is the one utilized by theLizardSquadhacking crew, theLizardStresser. Thirty 4 individuals who are alleged to have bought stressers and booter providers have been arrested as a part of the operation. Stressers and booter companies assist facilitate distributed denial of service assaults which in flip, flood servers and knock web sites offline.
“Booter and stresser services are a type of DDoS-for-rent, marketed in forum communications and obtainable on Dark Web marketplaces, providing malicious actors the power to anonymously attack any Internet-connected target. The providers received the title of "booter" as a result of initially they have been used by players to knock opponents off line who had bettered them in an internet battle, mentioned FBI particular agent Elliott Peterson.
This comparatively new Crime-as-a-Service pattern has created an entry level for novice DDoS attackers, offering a simple choice to anonymously attack almost any web site and forcing it offline for a small payment. One of the many Skype resolvers that had been publically availableThese Skype resolver providers ended up offering paid API subscription services that had been primarily sold to IP stresser homeowners so that they might create their own Skype resolver web page on their booter.
WebStresser was one of many so-known as “booter” or “stresser” companies — virtual hired muscle that even completely unskilled customers can rent to knock almost any website or Internet person offline. Want to run a Minecraft server from residence without revealing your IP address?
The finish goal for these booter homeowners was to help the shopper in obtaining their goal’s IP handle. What the craziest a part of this all to me was for a way long this vulnerability actually existed. ip stresser free trial was not until early 2016 when Microsoft’s Skype team released a weblog addressing the difficulty. So we're allowed, at any given time, to have up to 100 people inside our coffee shop. If we ever reach greater than that a hundred-particular person limit, we are unable to just accept this visitors, and thus a denial of service comes into action.

When these servers send data again to you, it goes to the proxy server, which then routes it to you. The problem with proxy servers is that many of the services on the market are fairly shady, spying on you or inserting adverts into your browser. A distributed denial of service assault (DDoS) is a particular kind of denial of service assault. The precept is the same, but the malicious traffic is generated from multiple sources -- although orchestrated from one central level. The incontrovertible fact that the visitors sources are distributed -- often all through the world -- makes a DDoS assault much harder to dam than one originating from a single IP tackle.
Europol’s European Cybercrime Centresaid Mondayit carried out the operation from Dec. 5 to 9. To give you an instance of the price-friendliness of this lovely service, one pattern Booter costs $40 USD/month (£25) for an unlimited number of DDoS attacks lasting one hour. According to the release, Downthem’s database showed over 2000 buyer subscriptions, and had been used to conduct, or attempt to conduct, over 200,000 DDoS assaults which have been carried out between October 2014 and November 2018.
# DDOSIM
How your computer acts when infected depends on what the cybercriminals are trying to accomplish. Many botnets are designed to harvest knowledge, corresponding to passwords, social safety numbers, bank card numbers, addresses, telephone numbers, and other private data. The data is then used for nefarious functions, corresponding to identification theft, credit card fraud, spamming, and malware distribution.
Bots may also be used to launch attacks on websites and networks, which as are sometimes referred to as Distributed Denial of Service Attacks or DDoS. In reality, in a latest survey practically half the responding companies mentioned that they believed that their opponents were launching DDoS assaults in order to disrupt services.
Just set up a free proxy with Amazon Web Services to guard your server from denial-of-service attacks. DDoSPedia is a glossary that focuses on community and software safety terms with many distributed denial-of-service (DDoS)-associated definitions. It provides a central place for onerous to search out web-scattered definitions on DDoS attacks.
Mythbusters: VPN for Gaming – Do You Really Need One?
After all, if your competition’s website is down, all the visitors will come to your website as an alternative. Additionally, your competition’s model image is tarnished, giving optimistic associations to your organization instead. A proxy server is an middleman server through which your visitors will get routed. The web servers you go to see solely the IP address of that proxy server and never your IP tackle.
Since then, he stated, many had diversified to supply "stresser" providers that attempt to overwhelm a target website with knowledge in what is named a distributed denial of service (DDoS) attack. The problem is that legal organisations are abusing booters for unlawful DDoS assaults, one of the most well-liked examples is the one utilized by theLizardSquadhacking crew, theLizardStresser. Thirty 4 individuals who are alleged to have bought stressers and booter providers have been arrested as a part of the operation. Stressers and booter companies assist facilitate distributed denial of service assaults which in flip, flood servers and knock web sites offline.
“Booter and stresser services are a type of DDoS-for-rent, marketed in forum communications and obtainable on Dark Web marketplaces, providing malicious actors the power to anonymously attack any Internet-connected target. The providers received the title of "booter" as a result of initially they have been used by players to knock opponents off line who had bettered them in an internet battle, mentioned FBI particular agent Elliott Peterson.
This comparatively new Crime-as-a-Service pattern has created an entry level for novice DDoS attackers, offering a simple choice to anonymously attack almost any web site and forcing it offline for a small payment. One of the many Skype resolvers that had been publically availableThese Skype resolver providers ended up offering paid API subscription services that had been primarily sold to IP stresser homeowners so that they might create their own Skype resolver web page on their booter.
WebStresser was one of many so-known as “booter” or “stresser” companies — virtual hired muscle that even completely unskilled customers can rent to knock almost any website or Internet person offline. Want to run a Minecraft server from residence without revealing your IP address?
The finish goal for these booter homeowners was to help the shopper in obtaining their goal’s IP handle. What the craziest a part of this all to me was for a way long this vulnerability actually existed. ip stresser free trial was not until early 2016 when Microsoft’s Skype team released a weblog addressing the difficulty. So we're allowed, at any given time, to have up to 100 people inside our coffee shop. If we ever reach greater than that a hundred-particular person limit, we are unable to just accept this visitors, and thus a denial of service comes into action.

When these servers send data again to you, it goes to the proxy server, which then routes it to you. The problem with proxy servers is that many of the services on the market are fairly shady, spying on you or inserting adverts into your browser. A distributed denial of service assault (DDoS) is a particular kind of denial of service assault. The precept is the same, but the malicious traffic is generated from multiple sources -- although orchestrated from one central level. The incontrovertible fact that the visitors sources are distributed -- often all through the world -- makes a DDoS assault much harder to dam than one originating from a single IP tackle.
