SPOILER ALERT!
2 Israeli teens arrested after DDoS 'booter' service vDOS hacked
To date, for instance, it's unclear if the document-setting DDoS attacks tied to contaminated internet of things gadgets - and IoT malware corresponding to Mirai - have been launched by stresser/booter services. But traditionally, cybercriminals have only infected large numbers of IoT gadgets to monetize their efforts by providing on-demand DDoS assaults. You stand a greater chance of withstanding a DDoS assault if your Web server is positioned in a hosting middle than should you run it yourself. That's as a result of its data heart will likely have far greater bandwidth links and higher capability routers than your organization has, and its workers will probably have extra expertise coping with assaults.
Booter and stresser companies are a form of DDoS-for-hire--- advertised in discussion board communications and out there on Dark Web marketplaces--- offering malicious actors the flexibility to anonymously assault any Internet-linked target. These providers are obtained by way of a financial transaction, normally in the form of online cost providers and virtual forex. IP booters, also called IP stressers, are companies that have been dropped at life within the early 2010s and gained big traction for the convenience of accessibility. These companies allowed for anybody to provoke DDoS attacks by renting another person’s infrastructure for a cheap month-to-month price — some as cheap as $2.
This analysis is still in its initial part and will contribute to a Ph.D. thesis after 4 years. An Ars analysis of theLizardStresser database found that the service launched nearly sixteen,000 individual attacks over the past month, targeting just over 3,900 IP addresses. ddos stresser free of those assaults—sixty seven %—targeted widespread Web server ports (port eighty and 8080 for HTTP; and a small however important variety of attacks on port 443 for HTTPS). The next most popular goal—accounting for nearly 7 % of the assaults—was port 25565, the network port used by Minecraft servers. Most booting companies at present are utilizing cloud-primarily based hosting to leverage their community.
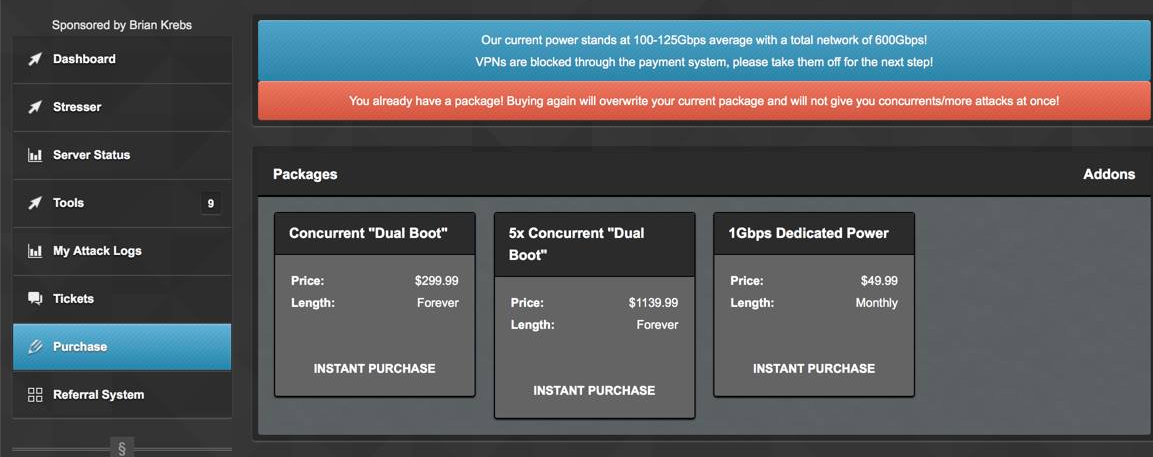
Distributed Denial of Service (DDoS) attacks are an growing risk on the Internet. Until a few years in the past, these types of assaults had been only launched by individuals with superior data of computer networks. However, these days the power to launch attacks have been supplied as a service to everyone, even to these with none advanced data. Some of them promote, for less than U$ 5, up to 25 Gbps of DDoS visitors, which is greater than sufficient to make most hosts and providers on the Internet unavailable. Booters are rising in recognition and they have shown the success of attacks towards third celebration services, corresponding to government web sites; nonetheless, there are few mitigation proposals.
In addition, present literature in this area supplies solely a partial understanding of the risk, for instance by analyzing just a few elements of one specific Booter. In this paper, we suggest mitigation options towards DDoS-as-a-Service that might be achieved after an intensive characterization of Booters. Early outcomes present fifty nine completely different Booters, which some of them don't deliver what is offered.
Having your Web server situated with a hoster may also keep DDoS traffic geared toward your Web server off your corporate LAN so at least that a part of your corporation – together with email and presumably voice over IP (VoIP) providers – should operate usually during an assault. Figures posted to the house page of Ragebooter.internet declare the service has been used to conduct greater than 310,000 DDoS assaults. Memberships are offered in packages ranging from $3 per day to $300 a year for an “enterprise” plan.
Ragebooter[dot]net includes a notice at the prime of the location indicating that rageservices[dot]internet is indeed affiliated with Ragebooter. DDoS (Distributed Denial of Service) attacks attempt to make servers or networks quickly unavailable to customers. Most of us would, indeed, suppose that solely folks with high technical skills would be able to carry out such assaults, however that is not true. ps4 booter can use the so known as ‘Booter’ web sites to disrupt on-line services and Jose Jair Cardoso de Santanna, a PhD candidate from the Design and Analysis of Communication Systems group, is aiming to mitigate that. DE-CIX’s Daniel Kopp presented preliminary outcomes at the RIPE77 assembly in Amsterdam last week.
For instance, ExoStresser was used to launch DDoS attacks towards a major video game producer, and a Pennsylvania scholar used BetaBooter to attack her college's network, also bringing down the IT systems of 17 different organizations in a domino effect. "DDoS attacks continue to develop in depth and complexity, with many attacks blending network and utility layer attacks," the IOCTA report reads. "Booters/stressers are readily available as-a-service, accounting for an rising number of DDoS assaults." Such providers are sometimes additionally used to extort victims. On-demand DDoS assaults could be robust to trace, especially if service operators use contaminated endpoints to launch their attacks.
By utilizing cloud providers to host their assault scripts they are able to provide bigger bandwidth for his or her attacks. Owners behind these stresser providers only have a couple of expenses to get their service up and running. These servers should enable IP handle spoofing, have a quick uplink, 1Gbps+, and have unmetered bandwidth usage. Once the proprietor has their servers, all they have to do is setup the service by importing the shell of their selection. US authorities began an investigation into Usatyuk's services after his websites were on the center of many DDoS attacks in 2016.
Booter and stresser companies are a form of DDoS-for-hire--- advertised in discussion board communications and out there on Dark Web marketplaces--- offering malicious actors the flexibility to anonymously assault any Internet-linked target. These providers are obtained by way of a financial transaction, normally in the form of online cost providers and virtual forex. IP booters, also called IP stressers, are companies that have been dropped at life within the early 2010s and gained big traction for the convenience of accessibility. These companies allowed for anybody to provoke DDoS attacks by renting another person’s infrastructure for a cheap month-to-month price — some as cheap as $2.
This analysis is still in its initial part and will contribute to a Ph.D. thesis after 4 years. An Ars analysis of theLizardStresser database found that the service launched nearly sixteen,000 individual attacks over the past month, targeting just over 3,900 IP addresses. ddos stresser free of those assaults—sixty seven %—targeted widespread Web server ports (port eighty and 8080 for HTTP; and a small however important variety of attacks on port 443 for HTTPS). The next most popular goal—accounting for nearly 7 % of the assaults—was port 25565, the network port used by Minecraft servers. Most booting companies at present are utilizing cloud-primarily based hosting to leverage their community.

Distributed Denial of Service (DDoS) attacks are an growing risk on the Internet. Until a few years in the past, these types of assaults had been only launched by individuals with superior data of computer networks. However, these days the power to launch attacks have been supplied as a service to everyone, even to these with none advanced data. Some of them promote, for less than U$ 5, up to 25 Gbps of DDoS visitors, which is greater than sufficient to make most hosts and providers on the Internet unavailable. Booters are rising in recognition and they have shown the success of attacks towards third celebration services, corresponding to government web sites; nonetheless, there are few mitigation proposals.
In addition, present literature in this area supplies solely a partial understanding of the risk, for instance by analyzing just a few elements of one specific Booter. In this paper, we suggest mitigation options towards DDoS-as-a-Service that might be achieved after an intensive characterization of Booters. Early outcomes present fifty nine completely different Booters, which some of them don't deliver what is offered.
Having your Web server situated with a hoster may also keep DDoS traffic geared toward your Web server off your corporate LAN so at least that a part of your corporation – together with email and presumably voice over IP (VoIP) providers – should operate usually during an assault. Figures posted to the house page of Ragebooter.internet declare the service has been used to conduct greater than 310,000 DDoS assaults. Memberships are offered in packages ranging from $3 per day to $300 a year for an “enterprise” plan.
Ragebooter[dot]net includes a notice at the prime of the location indicating that rageservices[dot]internet is indeed affiliated with Ragebooter. DDoS (Distributed Denial of Service) attacks attempt to make servers or networks quickly unavailable to customers. Most of us would, indeed, suppose that solely folks with high technical skills would be able to carry out such assaults, however that is not true. ps4 booter can use the so known as ‘Booter’ web sites to disrupt on-line services and Jose Jair Cardoso de Santanna, a PhD candidate from the Design and Analysis of Communication Systems group, is aiming to mitigate that. DE-CIX’s Daniel Kopp presented preliminary outcomes at the RIPE77 assembly in Amsterdam last week.
For instance, ExoStresser was used to launch DDoS attacks towards a major video game producer, and a Pennsylvania scholar used BetaBooter to attack her college's network, also bringing down the IT systems of 17 different organizations in a domino effect. "DDoS attacks continue to develop in depth and complexity, with many attacks blending network and utility layer attacks," the IOCTA report reads. "Booters/stressers are readily available as-a-service, accounting for an rising number of DDoS assaults." Such providers are sometimes additionally used to extort victims. On-demand DDoS assaults could be robust to trace, especially if service operators use contaminated endpoints to launch their attacks.
Understanding DDoS internals: Measuring booter providers
By utilizing cloud providers to host their assault scripts they are able to provide bigger bandwidth for his or her attacks. Owners behind these stresser providers only have a couple of expenses to get their service up and running. These servers should enable IP handle spoofing, have a quick uplink, 1Gbps+, and have unmetered bandwidth usage. Once the proprietor has their servers, all they have to do is setup the service by importing the shell of their selection. US authorities began an investigation into Usatyuk's services after his websites were on the center of many DDoS attacks in 2016.
